=======================================================================
Cybernetics in the 3rd Millennium (C3M) Volume 13 Number 1, Nov. 2016
Alan B. Scrivener — www.well.com/user/abs — mailto:abs@well.com
========================================================================
 illustration from Unspy blog
(unspy.wordpress.com/tag/fourth-amendment/)
In this issue:
illustration from Unspy blog
(unspy.wordpress.com/tag/fourth-amendment/)
In this issue:
Short Subjects
 "Fractured Flickers" letterhead with Theda Bara
(artofjayward.blogspot.com/2015/06/fractured-flickers.html)
"Fractured Flickers" letterhead with Theda Bara
(artofjayward.blogspot.com/2015/06/fractured-flickers.html)
- Nora Bateson's new book
 On October 23, 2016 a new book by Nora Bateson, daughter of Gregory Bateson,
became available on Amazon: "Small Arcs of Larger Circles: Framing Through
Other Patterns."
( www.amazon.com/exec/obidos/ASIN/1909470961/hip-20 )
She also has a blog at:
norabateson.wordpress.com/
and is on Facebook.
On October 23, 2016 a new book by Nora Bateson, daughter of Gregory Bateson,
became available on Amazon: "Small Arcs of Larger Circles: Framing Through
Other Patterns."
( www.amazon.com/exec/obidos/ASIN/1909470961/hip-20 )
She also has a blog at:
norabateson.wordpress.com/
and is on Facebook.
- Systems, Man,and Cybernetics 2017
The 2017 IEEE International Conference on Systems, Man, and
Cybernetics (SMC2017) will be held at the Banff Springs Resort, Banff,
Alberta, Canada, 01 Oct - 04 Oct 2017. Abstract submission deadline:
01 Apr 2017.
( www.ieee.org/conferences_events/conferences/conferencedetails/index.html?Conf_ID=34148 )
- System Dynamics Society 2017
The 35th International Conference of the System Dynamics Society will be held
at Cambridge, Massachusetts, USA, 16 July - 20 July 2017.
"2017 marks the 60th anniversary of the founding of the field of System
Dynamics. It is thus fitting that we hold the 60th anniversary conference
in Cambridge, next to the MIT campus where Jay Forrester developed the field."
( conference.systemdynamics.org/ )
 NY Times photo
(Note: in the few weeks since I typed the above, Dr. Forrester passed away.
www.nytimes.com/2016/11/18/technology/jay-forrester-dead.html?_r=0
I will have more to say about this remarkable man in an upcoming 'zine.)
NY Times photo
(Note: in the few weeks since I typed the above, Dr. Forrester passed away.
www.nytimes.com/2016/11/18/technology/jay-forrester-dead.html?_r=0
I will have more to say about this remarkable man in an upcoming 'zine.)
An Update on Uncrackable Encryption for the Masses
 illustration for "What Is Encryption?" from wiseGEEK
( www.wisegeek.com/what-is-encryption.htm )
illustration for "What Is Encryption?" from wiseGEEK
( www.wisegeek.com/what-is-encryption.htm )
"The new world of the internet, abstracted from the old world of brute atoms,
longed for independence. But states and their friends moved to control our new
world -- by controlling its physical underpinnings. The state, like an
army around an oil well, or a customs agent extracting bribes at the border,
would soon learn to leverage its control of physical space to gain control
over our platonic realm... The state would leech into the veins and arteries
of our new societies, gobbling up every relationship expressed or communicated,
every web page read, every message sent and every thought googled, and then
store this knowledge, billions of interceptions a day, undreamed of power, in
vast top secret warehouses, forever. It would go on to mine and mine again
this treasure, the collective private intellectual output of humanity, with
ever more sophisticated search and pattern finding algorithms... And then the
state would reflect what it had learned back into the physical world, to start
wars, to target drones, to manipulate UN committees and trade deals, and to do
favors for its vast connected network of industries, insiders and cronies.
But we discovered something. Our one hope against total domination. A hope
that with courage, insight and solidarity we could use to resist. A strange
property of the physical universe that we live in.
The universe believes in encryption.
It is easier to encrypt information than it is to decrypt it.
We saw we could use this strange property to create the laws of a new world.
To abstract away our new platonic realm from its base underpinnings of
satellites, undersea cables and their controllers. To fortify our space
behind a cryptographic veil. To create new lands barred to those who control
physical reality, because to follow us into them would require infinite
resources.
And in this manner to declare independence."
— Julian Assange (2012) "Cypherpunks: Freedom and the Future
of the Internet"
( www.amazon.com/exec/obidos/ASIN/1939293006/hip-20 )
My buddy Wayne H. and I have been making progress on the vision of
affordable, available technology for anyone to secure their emails
with encryption which is provably, mathematically, impossible to crack.
For the initial description see my article "Uncrackable Encryption for the
Masses" in C3M v. 12 n. 1, July 2015.
(
www.well.com/user/abs/Cyb/archive/c3m_1201.html#sec_1 )
PROGRESS SO FAR
 Dilbert cartoon
( https://www.random.org/analysis/ )
Dilbert cartoon
( https://www.random.org/analysis/ )
"Any one who considers arithmetical methods of producing random digits is,
of course, in a state of sin."
— John von Neumann
The first step in the workflow was generating the random bits. I already
had a prototype encryption program, but no good way to generate keys for it.
I consulted the Wikipedia page on hardware random number generators,
(
en.wikipedia.org/wiki/Hardware_random_number_generator )
and then ordered a gizmo called a FST-01 for testing, for about $35 from a
supplier called Seeed.
(
www.seeedstudio.com/ )
The Hardware Problem
My first surprise came when I got the tracking number and saw it was shipping
from China, and for a while it was held up in customs. This was frustrating
for the time lost, but also because I wanted something made domestically for
the final product, to avoid any entanglements with munitions export rules.
The next surprise came when, shortly before the unit arrived, I discovered
that my trusty Linux system (which was now a teenager) had a hard drive
failure. Oh, drat. It looked like that was the easiest system to test on.
(
www.gniibe.org/FST-01/q_and_a/neug-standalone-device.html )
Meanwhile, I read some on-line documentation and got thoroughly confused.
(
wiki.seeedstudio.com/wiki/FST-01 )
This is when I called up my buddy Wayne H., who is a very talented hardware
guy, and asked him for help. I told him the docs looked like they were
describing how they built the unit, not how I was supposed to use it.
He came to the rescue. He figured out that the thingy I'd bought needed to
be programmed with firmware called NeuG, and mine wasn't.
(
www.gniibe.org/memo/development/gnuk/rng/neug.html )
My options were to buy another SFT-01 with the NeuG firmware pre-installed
(abut $50), or buy a gizmo to program mine (much more expensive), or find
another solution. Well, I didn't like the idea of there being a little
computer program running on my gizmo, because that's one more security
hole, so I thought it about it.
Meanwhile, independently, Wayne had been experimenting with building his
own circuits for generating random numbers, using various recipes on the
internet. The noisy diode-based solutions kept generating 60-cycle hum,
which is all around us due to our power grid. He realized he needed to "tune
out" the signals he didn't want. Then he hit on an amazingly simple idea.
He took a cheap transistor radio, tuned it between stations so it made that
sound ("ffffff") which is close to white noise, and plugged it into the audio
input jack of his laptop.
His other brainstorm was that to "whiten" the data (make the noise whiter
by making the number of zeros and ones about even) he should apply the
same algorithms done by the NeuG code in the SFT-01 device: a Cyclic Redundancy
Check algorithm called CRC32,
(
en.wikipedia.org/wiki/Cyclic_redundancy_check )
followed by a "hash" algorithm called SHA-256.
(
en.wikipedia.org/wiki/SHA-2 )
Testing for Randomness
The he contacted me and said he had some bits he thought were random, but how
could we tell for sure?
I went a-Googling to find the answer, and on Stack Overflow
(
stackoverflow.com/questions/4027756/random-number-analysis )
I found these answers:
Given a series of randomly generated data how can I figure out how random
it actually is?
* * * * * *
Run --- don't walk --- to a bookstore and buy Knuth's The Art of Computer
Programming, volume II, Semi-Numerical Algorithms. Until you read that,
you're just flying blind.
* * * * * *
The DieHarder test battery by Robert G. Brown --- which reimplements and
extends the old DIEHARD by Marsaglia et al -- has been wrapped into the
R package RDieHarder which you could start with.
* * * * * *
Edit Also, for the subset of cryptographic tests, the NIST suite (which
is included in DieHarder) should be appropriate as that is what it was
designed for.
I've known about Knuth's epic multi-volume tome but I've never read it.
Searching online, I found that volume two was at the San Diego central library,
and I drove downtown to get it.
"Art of Computer Programming, Volume 2: Seminumerical Algorithms" (1969)
by Donald E. Knuth
(
www.amazon.com/exec/obidos/ASIN/0201896842/hip-20 )
Chi Square
Section 3.3.1 educated me about the Chi-square test. I've heard of it
all my adult life, but never quite knew what it was. I thought it had to
do with some kind of 4x4 matrix, like a quaternion. Completely wrong.
(
en.wikipedia.org/wiki/Chi-squared_distribution )
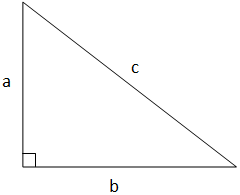
It actually involves calculating how close a set of numbers is to an
average expected distribution, using what looks to me like a Pythagorean
distance formula for n dimensions. Surely you recall Pythagoras' theorem,
so famous even the scarecrow in the Wizard of Oz was familiar with it.
As reported in a web page on the Pythagorean Theorem in movies,
(
www.regentsprep.org/regents/math/geometry/gp13/TResourcePyth.htm )
After receiving his brain from the wizard, the Scarecrow recites the
Pythagorean Theorem incorrectly. He stated, "The sum of the square roots of
any two sides of an isosceles triangle is equal to the square root of the
remaining side." Oops!
The correct formula is of course
a2 + b2 = c2
or as I write it like a programmer,
a^2 + b^2 = c^2
Alternately solving for c we get:
c = sqrt(a^2 + b^2)
(sqrt is a square root function.) That's the formula for two dimensions,
relating sides a, b and c (hypotenuse) of a right triangle.
So if we have two points,
p1 and
p1, with coordinates:
p1 = {x1, y1}
p2 = {x2, y2}
the distance between them will be:
d = sqrt((x2 - x1)^2 + (y2 - y1)^2)
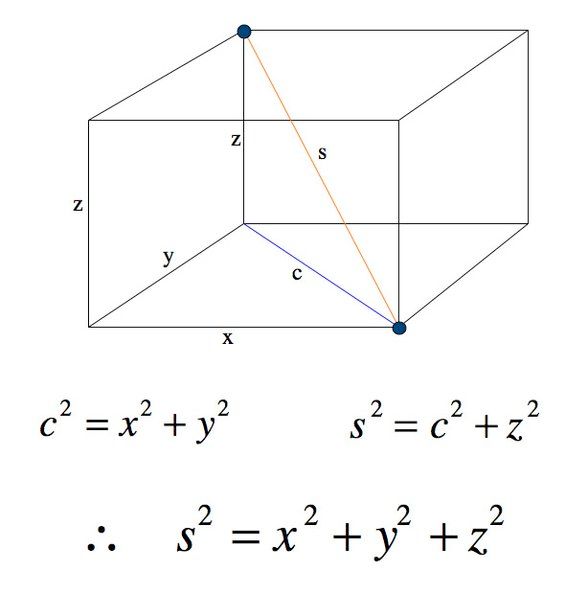
Well, it turns out that you an extend this to three dimensions. If you have
two points in 3D with coordinates:
p1 = {x1, y1, z1}
p2 = {x2, y2, z2}
3d distance illustration from Pacific Learning Academy
( www.pacificlearningacademy.com/the-3d-pythagorean-theorem )
the distance between them will be:
d = sqrt((x2 - x1)^2 + (y2 - y1)^2 + (z2 - z1)^2)
Still with me? Because it turns out you can generalize the Pythagorean
distance formula to any number of dimensions. Beyond three dimensions
you lose the ability to visualize the problem as a physical model, but
the math is trivial. This turns out to be useful not only in high-dimension
physics like General Relativity, but also in statistics, where n-dimensional
coordinates can represent the state of a system or a set of measurements, and
the n-dimensional distance means something about how close or similar two such
states are. The Chi Square is an example of this. Every possible distribution
of events is represented as an n-dimensional point.
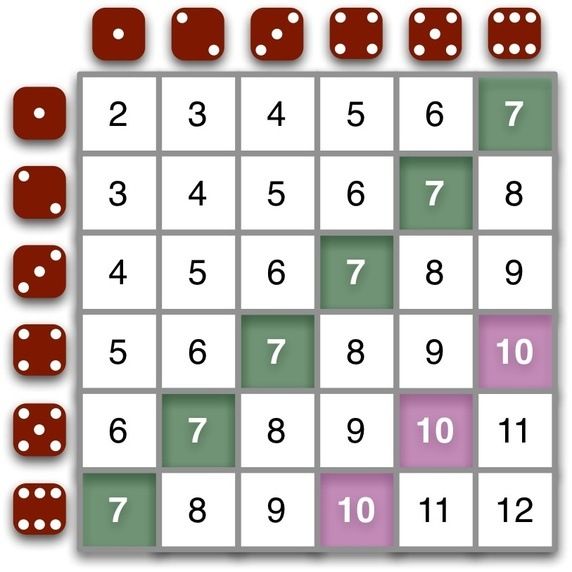
Knuth used the example of rolling two dice. You may have seen this
illustration of the possible outcomes:
distribution of rolls of two dice, from Quora
( www.quora.com/What-is-the-probability-of-getting-a-sum-of-6-if-two-dice-are-thrown )
Out of 36 possible pairings 6 result in a seven being thrown, so the probability
is 6/36, or 1/6. For rolling a ten the probability is 3/36, or 1/12. If you
roll a pair of dice 144 times ("one gross") the expected distribution is
144*1/6, or 24 rolls of seven, and 144*1/12, or 12 rolls of ten. But in
actual practice the numbers will usually be slightly off. The measure of
distance between the expected and actual is called Chi, and Chi squared
is a number usually called V. I think statisticians use V because it saves
them from having to compute a square root at the end, and they can compare
V values just as easily.
The last step in the Chi Square algorithm is to compute a probability that
the observed value of V was generated by a random process. This is the
gnarly step, involving computing something called the upper and lower gamma
functions.
(
en.wikipedia.org/wiki/Gamma_distribution )
I decided not to wade into this, since luckily Wolfram Alpha will give me
the values for any given distribution, and I only needed to find them once.
It told me that for a random string of bytes, each having 256 possible values,
- the probability that V is less than 226.52 is 10%,
- the probability that V is less than 239.462 is 25%,
- the probability that V is less than 254.334 is 50%,
- the probability that V is less than 269.847 is 75%,
- the probability that V is less than 284.336 is 90%,
and, conversely,
- the probability that V is greater than 226.52 is 90%,
- the probability that V is greater than 239.462 is 75%,
- the probability that V is greater than 254.334 is 50%,
- the probability that V is greater than 269.847 is 25%,
- the probability that V is greater than 284.336 is 10%,
I wrote a program that computed V for a sequence of bytes, and then looked
up the probability range in a table of values from Wolfram Alpha. For shorter
sequences (about 250 kilobytes) I was getting poor results, but for the longest
sequence (10,030,232 bytes, or about 10 megabytes) it was pretty good, with a
probability of being the result of a random process being between 25% and 50%,
which is as good as it gets with Chi Square tests. I also did a visualization
(using background colors of a Table in HTML) and here is one example below.
Since I'm showing intermediate values in the algorithm that are normally not
analyzed separately, I'm not sure what it means, but it's nice to see something
tangible. Each cell represents one possible value of the bytes, from 0 (upper
left) to 255 (lower right), showing the square of the difference between the
measured value and a perfect distribution; when added together all 256 values
give V.
| 0.105873 | 1.016770 | 2.349514 | 0.160930 | 0.048088 | 0.031995 | 1.186319 | 0.371175 | 0.002258 | 0.503155 | 0.510348 | 0.004587 | 0.317840 | 0.090642 | 0.732467 | 0.279216 |
| 0.152926 | 0.976425 | 0.681501 | 0.195828 | 2.719230 | 0.034178 | 0.365045 | 0.886850 | 0.504500 | 0.633880 | 0.357831 | 4.972857 | 0.044156 | 0.195828 | 1.628449 | 0.232318 |
| 0.488923 | 0.917439 | 1.197349 | 4.579606 | 0.109186 | 0.102611 | 0.888635 | 0.363901 | 0.294434 | 0.935064 | 0.106490 | 0.812361 | 0.038016 | 1.089340 | 0.001472 | 1.549646 |
| 0.052621 | 3.830560 | 1.537093 | 0.030214 | 0.474895 | 0.002864 | 2.960754 | 0.115966 | 0.105873 | 0.174110 | 0.625861 | 2.857358 | 0.741140 | 1.574904 | 3.596930 | 0.000065 |
| 0.149732 | 0.109813 | 0.706754 | 0.165009 | 2.081740 | 0.007900 | 0.070599 | 0.067940 | 0.137529 | 0.339929 | 2.430543 | 0.165009 | 3.426532 | 0.076070 | 5.090428 | 1.264605 |
| 0.023889 | 3.009854 | 0.616405 | 1.368934 | 0.371175 | 0.814070 | 0.317840 | 0.048504 | 0.001472 | 0.812361 | 1.333699 | 0.161691 | 1.078820 | 0.462358 | 0.524886 | 2.891619 |
| 0.944860 | 0.030214 | 0.130137 | 0.064848 | 0.057813 | 0.030544 | 4.236277 | 1.175339 | 0.268640 | 0.879135 | 1.310463 | 1.680433 | 0.917439 | 0.109813 | 0.027114 | 0.130822 |
| 0.218823 | 1.502063 | 0.004716 | 1.404630 | 0.020868 | 1.600366 | 2.067187 | 0.042058 | 0.015203 | 0.035712 | 5.438120 | 2.978165 | 0.517591 | 0.156903 | 0.345845 | 0.015203 |
| 1.037249 | 0.503155 | 0.169139 | 0.624363 | 0.295463 | 5.018023 | 0.000004 | 0.706754 | 0.048088 | 0.650071 | 1.651903 | 0.698285 | 1.142706 | 1.262476 | 1.759940 | 3.045015 |
| 0.043758 | 1.298922 | 1.800382 | 0.009799 | 0.190555 | 0.106490 | 0.776342 | 0.160930 | 0.000539 | 0.045897 | 0.017797 | 0.218823 | 1.285283 | 2.321527 | 1.452938 | 3.873941 |
| 1.253268 | 0.001400 | 0.165780 | 0.497349 | 1.921839 | 4.302825 | 0.006206 | 0.650071 | 0.177552 | 3.223882 | 3.374130 | 3.281969 | 0.396206 | 1.880047 | 2.349514 | 0.925319 |
| 0.096828 | 2.049972 | 0.691442 | 0.062774 | 1.333699 | 0.511702 | 0.839911 | 1.004708 | 0.018050 | 0.084110 | 1.600366 | 0.004048 | 0.447451 | 2.110998 | 0.435285 | 2.943394 |
| 0.045897 | 0.723845 | 0.142015 | 0.345845 | 0.000296 | 1.014861 | 0.072797 | 0.045897 | 0.173320 | 1.219564 | 0.994605 | 0.650071 | 0.090642 | 2.321527 | 0.073309 | 0.084660 |
| 0.758639 | 0.554576 | 0.577379 | 0.382416 | 4.194787 | 0.060268 | 0.454236 | 0.222680 | 0.062774 | 8.509263 | 0.019170 | 0.316773 | 0.062774 | 0.013029 | 0.045897 | 0.044156 |
| 0.749864 | 1.097925 | 0.812361 | 0.563547 | 3.191083 | 0.181835 | 0.434036 | 1.465143 | 0.003321 | 2.170128 | 4.972857 | 0.001110 | 0.096828 | 0.000539 | 2.303281 | 0.022353 |
| 0.119432 | 1.173286 | 0.600641 | 1.110533 | 0.106490 | 0.043758 | 1.811414 | 0.152926 | 0.624363 | 0.099400 | 0.299942 | 0.300981 | 0.674740 | 0.288977 | 4.323809 | 3.333652 |
KEY:
| BAD |
POOR |
GOOD |
GOOD |
POOR |
BAD |
V = 241.200881
For comparison, I looked at the Chi Square of a JPEG file, which is generally
compressed and so I thought it would be pretty close to random. So wrong.
The average V here is off by about ten million per cent, and my table for
converting V values to probabilities doesn't go anywhere near high enough to
find the probability of it being randomly generated, but it's safe to say it's
astronomically low.
| 163363.071032 | 15306.006086 | 12780.926124 | 11525.105891 | 15949.899789 | 11482.355567 | 14123.528240 | 8797.118955 | 16521.561690 | 13995.075833 | 6972.468034 | 14220.862010 | 9096.786475 | 12250.437002 | 13216.702673 | 2238.414989 |
| 15101.857601 | 10931.692691 | 10513.685302 | 12067.871266 | 8145.367415 | 1533276.687652 | 11315.409844 | 12734.751432 | 8872.046635 | 7840.204741 | 11300.194816 | 10880.461924 | 8194.327029 | 13646.648213 | 6626.134630 | 664.202539 |
| 12024.124952 | 10983.043786 | 10568.248378 | 7420.651667 | 7682.640104 | 9866.897555 | 10420.626188 | 4854.395856 | 10977.689099 | 5741.835659 | 1529621.542003 | 4790.520989 | 9495.849167 | 7920.041595 | 8968.572568 | 3709.997522 |
| 10912.467053 | 2928.257333 | 4953.158928 | 9414.359669 | 6733.887888 | 8514.725703 | 7866.469935 | 6993.819171 | 8398.187329 | 7640.595204 | 13445.624600 | 11205.873738 | 5323.799372 | 10672.518437 | 4636.163309 | 8064.242242 |
| 15531.897723 | 10492.737106 | 13342.720653 | 7394.263374 | 15544.637356 | 9363.854298 | 10164.528150 | 4531.680668 | 9608.721064 | 7636.129132 | 7482.407141 | 7106.232766 | 6548.164125 | 7973.795053 | 5803.957015 | 482.281298 |
| 9052.974958 | 9087.041443 | 6011.328940 | 3742.438361 | 3867.891258 | 1597205.051214 | 1303.240915 | 1376852.455518 | 6619.480876 | 7750.871703 | 4959.634545 | 5972.564357 | 4835.899665 | 1223082.508388 | 3009.558480 | 175.787262 |
| 12097.079605 | 9151.455168 | 1366630.149901 | 4936.629348 | 5709.355748 | 6553.127178 | 6897.571696 | 11645.008815 | 13059.729046 | 3768.743670 | 10317.597003 | 5500.481886 | 8192.476833 | 7113.126756 | 10897.525477 | 1673.545518 |
| 12710.543169 | 3352.401446 | 5672.348656 | 8469.518815 | 15104.369597 | 12517.706196 | 1249582.491045 | 12345.640309 | 5187.473906 | 3232.772436 | 6952.001651 | 11939.103951 | 3576.754878 | 6466.545188 | 1080.494288 | 25738.528345 |
| 15516.617057 | 9283.919082 | 14794.475223 | 10861.281408 | 14200.150617 | 9063.674674 | 7379.330872 | 4386.999334 | 10467.626846 | 9156.344266 | 1517977.053155 | 10019.763104 | 7899.136106 | 9772.711035 | 8598.865199 | 44.374208 |
| 8123.245280 | 7203.920198 | 7221.279468 | 3550.520539 | 8497.759019 | 5040.573880 | 6276.472106 | 1811.749323 | 4032.968512 | 5786.840322 | 4881.492257 | 4296.760500 | 7531.995770 | 11392.729361 | 9502.821856 | 26.668450 |
| 13664.562617 | 9270.137849 | 14026.528713 | 6849.275117 | 9827.344989 | 5028.971009 | 4845.143348 | 1017.933644 | 7650.425160 | 4095.516517 | 1261.519930 | 1452466.595630 | 5305.173093 | 3523.169404 | 1283743.663606 | 120.098668 |
| 10240.919583 | 1321500.548382 | 7813.080070 | 9227.873777 | 8522.271883 | 7004.079310 | 7595.993234 | 3785.702873 | 6269.187101 | 6552.299872 | 13804.698248 | 1237524.574582 | 3170.319322 | 7645.956215 | 5600.989832 | 1716.813492 |
| 9421.302380 | 15121.959416 | 9993.182222 | 4749.581337 | 4971.157198 | 1512969.648231 | 7621.846474 | 1116.056298 | 5832.801184 | 3067.018459 | 5856.240835 | 1629.108376 | 3252.559673 | 2202.296912 | 14016.847143 | 6626.966584 |
| 13853.974764 | 10867.673033 | 8449.778639 | 1594.234001 | 7772.481194 | 8635.865669 | 8900.949578 | 2569.957423 | 1283164.747241 | 9612.728750 | 11203.710085 | 4910.812426 | 8395.377801 | 12416.145789 | 7758.971737 | 382.161740 |
| 11862.175089 | 5258.379636 | 81.032446 | 2463.828388 | 3159.969694 | 1139.394124 | 450.286098 | 8078.172659 | 12094.831556 | 4597.275860 | 6167.641203 | 5106.819469 | 1266904.564701 | 8374.788959 | 9828.358165 | 4428.388817 |
| 5093.681634 | 1.091121 | 263.163381 | 370.071561 | 3095.383571 | 1376.558339 | 6424.698831 | 3177.228475 | 7.910981 | 546.175641 | 82.511122 | 774.071353 | 7807.505564 | 1703.711181 | 26661.575878 | 112452.450271 |
KEY:
| BAD |
POOR |
GOOD |
GOOD |
POOR |
BAD |
V = 22841355.047908
Discrete Fourier Transform
I was also worried about the source of the signal — erratic radio
waves — having some periodic waves, especially 60-cycle "hum" from our
AC electrical system, so I found some Java code to perform a Discrete Fourier
Transform (DFT) to sort out the wavelengths. (This is sometimes called a Fast
Fourier Transform, or FFT, but that's just to speed up the calculation, and I
wasn't using that flavor.)
(
https://en.wikipedia.org/wiki/Discrete_Fourier_transform )
I took each complex result and found its length, so I was looking at amplitude
and ignoring phase, and then I set a pixel from black, through grey to white
based on the value (ranging from zero to two) and arranged them in a rectangle
for 4,096 frequency values. At first I was puzzled that the result looked
random, since I was expecting "all frequencies" to be present. Wayne said
the same thing. But then I realized if the output were always the same then
the input would have to always be the same, i.e. the reverse Fourier Transform
to recover the original signal would always give the exact same numbers, and
that's the opposite of random. So I came to accept that the frequency
distribution looked good.
 4096 frequencies as brightness values
4096 frequencies as brightness values
Do It Yourself
Once the random bits for the key have been generated, the next step in the
workflow is the encoding and decoding of messages. This will be done with
a program that we have yet to complete, but we have a working prototype
that just does the
exclusive or step, and we have tested the encrypting,
emailing, and decrypting of files using it. The source code for this
prototype is at:
www.well.com/user/abs/Crypto/xor.ALL
(where it has been for 17 years).
Though there is still work for us to do to make this system easy-to-use
and seamless from end-to-end, we have tested all the technical steps and
see no reason why it wouldn't work. If you are a mathematically-inclined
computer programmer (or if you have one available to work for you) there
is enough information in the last article and this one for you to implement
and use a one-time-pad encryption system with random bits from a radio
or other source.
FUTURE PLANS
 money growing on trees?
money growing on trees?
(
www.digitaltrends.com/cool-tech/amazon-kickstarter-site/ )
"This rule makes changes to (b)(1)(ii), (b)(1)(iii) and (b)(2) to harmonize
with changes to encryption procedures under sections 740.17 and 742.15(b).
Paragraph (v) is added to section 734.4(b)(1) to indicate that encryption
commodities and software may be considered for de minimis treatment if such
products were authorized for export under License Exception ENC after
submission of an encryption registration pursuant to section 740.17(b)(1)
of the EAR. "
— summary of Section 734.4 of the Export Administration Regulations (EAR)
Moving forward here is a partial "to do" list for our project:
- design and implement a prototype user-friendly software system for
generating keys, including writing them in pairs to USB drives along with
initialized "map" files for keeping track of key usage
- design and build a hardware prototype for key generation, based on
Raspberry PI, Arduino or a similar small cost system
- design and implement a prototype user-friendly software system for
encoding and decoding messages, as described in the spec in the previous
article on this topic, in C3M v. 12 n. 1 (see link above).
- perform more technical and usability tests, and answer the following questions:
- Are the bits really random?
I still need to get the Dieharder package in the R statistical language
running (which turns out to be quite a trick, since I have to compile
C source code first), and then perform the NIST test suite which seems
to be the gold standard in random number verification.
( csrc.nist.gov/groups/ST/toolkit/rng/documents/SP800-22rev1a.pdf )
I also want to run a Fourier Transform on the raw bits, before the CRC and
hash are applied, to see what kind of wave are in the raw audio signal from
the AM radio.
- Can we get people to do it?
Everyone I've I talked to who has an opinion says no, the logistics are
too much of a hassle. Even as the financial and reputational costs of
security breaches continue to rise, people at all levels (users, managers,
even government leaders) seem to be resisting all attempts to improve
their cybersecurity if it involves any inconvenience. Sigh. But still
I persist.
- Can others crack our encrypted messages?
I'm thinking some type of tiger-team effort and/or contest might help
settle this. I'm not arrogant enough to think we can solve this by
pure analysis.
- There are a few other miscellaneous things on our task list:
- Notify the Bureau of Industry and Security
According to Wikipedia (and I hope they are giving me the straight dope
here) we need to notify the Bureau of Industry and Security, a division
of the Department of Commerce, before releasing open-source software for
strong encryption. I need to figure out what form to fill out to do this.
- Post open source code
We will probably put the source code for key generation as well as
encryption/decryption on GitHub.
- Explore hardware alternatives to an AM radio
Ever the hardware tinkerer, Wayne has gone on to implement a hardware
solution that has advantages over the AM radio as a source of noise.
He's built a prototype and blogged about it:
( sites.google.com/site/wayneholder/white-noise-for-random-numbers )
This solution also needs testing for randomness. Stay tuned.
- Kickstarter project
As stated previously, we plan at some point to launch a Kickstarter
project for moving from the hardware prototype stage to manufacturing
turn-key systems for key-generation.
- Alternatives to USB drives
Wayne pointed out that using USB drives to distribute the keys adds a security
risk: the drives themselves can be vectors for malware. Ideally what would
work seamlessly is a device to emulate a USB drive, but one that delivers the
key bytes on demand only once, and then erases them. Possibly a gizmo like
the FST-01 but with different microcode could work. Of course there'd have
to be some way to get the bits into the device first. More research
is needed. If this works it could be our second Kickstarter project.
THE REST OF THE PROBLEM
 cyberthief
cyberthief
(
www.hackguide4u.com/2010/09/huge-collection-of-hacking-ebooks.html )
"...closing the stable door after the horse has bolted..."
— rural American expression
As I've previously mentioned, this plan only secures email in transit.
If you want to avoid being hacked like many campaign officials in this
last election you have to take other measures.
I'm reading Julian Assange's book now (see link above), and I learned that he
co-developed a "rubber hose" encryption system for file systems. That means if
someone beats you with a rubber hose demanding your encryption key, you can
give them a false key which decodes your cyphertext into a false plaintext.
The term
rubber hose encryption is now a real technical term.
(
en.wikipedia.org/wiki/Rubberhose_(file_system) )
In the case of Assange and company's system, it actually secures an entire
file system, and with a false key you have it decrypt to a different,
innocuous file system.
Just recently I learned about another file system encryption system, from
a local San Diego company called Fhoosh.
(
www.fhoosh.com )
These are types of solutions that can help secure an internal network from
malevolent hackers and other bad actors.
A PARANOID NOTE
 the eye in the triangle
the eye in the triangle
(
www.pinterest.com/magda1316/illuminati/ )
"These urban myths can be attractors, they pick up little fragments of
strangeness from everywhere, after a while nobody can look at the whole
thing and believe it all, it's too unstructured. But somehow we'll still
cherry-pick for the intriguing pieces — God forbid we should be taken in of
course, we're too hip for that — and yet there's no final proof that some of
it isn't true. Pros and cons, and it all degenerates into arguments on the
Internet, flaming, trolling, threads that only lead deeper into the labyrinth."
— Thomas Pynchon (2013, novel) "Bleeding Edge"
( www.amazon.com/exec/obidos/ASIN/1594204233/hip-20 )
I waited until after the U.S. election to write this, but upon reflection
it doesn't really matter much. I worry that if this project were to succeed
beyond my wildest dreams, I would make some powerful enemies, in the political
class, law enforcement, the intelligence community and the military-industrial
complex. Clinton scared me more than Trump, but only a little. The political
conspiracy web site What Really Happened
(
www.whatreallyhappened.com/RANCHO/POLITICS/BODIES.php )
reminds us that on April 18, 2016, Julian Assange's lawyer jumped, fell
or was pushed in front of a commuter train. On August 2, 2016 lawyer Shawn
Lucas, who sued the Democratic National Committee on behalf of Bernie Sanders
supporters, was found dead under suspicious circumstances.
As far as our new president-elect goes, the Techdirt web site
(
www.techdirt.com/articles/20161108/22473036002/what-election-means-stuff-techdirt-cares-about.shtml )
had this to say on November 8th:
Encryption: I don't believe Trump weighed in specifically on the whole 'going
dark' debate, but given his comments on mass surveillance and supporting law
enforcement over all else, I'm guessing that the chances of a bill banning
encryption just got a hell of a lot stronger. Download some strong encryption
software now and learn how to use it, folks.
Though it does not encrypt file systems, our plan is also a "rubber hose"
system because you can provide a false key to decrypt a message to any
alternative file you wish (of equivalent size). I sincerely hope no one is
ever beaten with a rubber hose or otherwise harmed for using it.
Let me add that I have absolutely no intention of killing myself, and if
I die suspiciously I want you all to assume I was assassinated by the
Illuminati or someone like them.
"If It's Just a Virtual Actor,
Then Why Am I Feeling Real Emotions?"
(Part Seven)
(If you haven't read parts one through six, see the archives, listed at the end.)
OTHER TRIPS
 got the tee shirt
got the tee shirt
- AVS '94 May 2-4, 1994
Rumor was that the '93 AVS user group conference was a financial fiasco,
with the company having to cover a lot of unsold hotel rooms, which is why
the employees all got upgraded to rooms at the Dolphin. For '94 the
company moved some of the conference management in-house and located it
in nearby Boston to save travel expenses for its employees.
The big announcement there was a new product, AVS Express, which would
replace the current version of AVS 5, and had been in secret development
for several years under the code name "IVAN," mostly worked on by
chief architect Jeff Vroom.
There was also a great homebrew beer Special Interest Group (SIG), which
had visitors from around the world bringing homebrew and microbrew beers
to sample.
- Grateful Dead in Las Vegas 6-26-94
As a child of the sixties I was actually never much of a Grateful Dead
fan, leaning more towards Jefferson Airplane, Doors, Iron Butterfly, etc.
But I had so many friends, especially in high tech, who were huge fans
("Deadheads" they called it) that I paid attention, and made it with some
friends to my second Grateful Dead concert at the University of Nevada Las
Vegas stadium for one of three nights. (The serious deadheads were there
for all three).
( archive.org/details/gd94-06-26.sbd.ladner.14943.sbeok.shnf )
As a result of this Vegas trip I ended up buying two CDs: a collection of
Grateful Dead covers called "Deadicated" (audio album, 1991) various artists
( www.amazon.com/exec/obidos/ASIN/B000002VHS/hip-20 )
and "Honeymoon in Vegas" soundtrack (audio album, 1992) various artists,
which consisted of a collection of Elvis covers.
( www.amazon.com/exec/obidos/ASIN/B0000028QF/hip-20 )
SIGGRAPH PREP
 SIGGRAPH '94 logo
SIGGRAPH '94 logo
"The best time to go [to Walt Disney World], if you want to avoid huge crowds,
is 1962."
— Dave Barry "The Only Travel Guide You'll Ever Need" (1999)
( www.amazon.com/exec/obidos/ASIN/0345431138/hip-20 )
My participation is the SIGGRAPH conferences over the last 33 years has led me
to ask myself some questions I might otherwise not have, questions like "I
wonder what it's like in Detroit in July?" and "I wonder what it's like in
Boston in July?" and "I wonder what it's like in Dallas in August?" and "I
wonder what it's like in Las Vegas in July?" and "I wonder what it's like
in Chicago in July?" The approach of the 1994 conference had me asking a new
question, "I wonder what it's like in Orlando in July?"
The ACM Conference on Computer Graphics and Interactive Techniques had never
been to Orlando before. I could almost feel the vendors salivating for the
chance to get mindshare in an emerging market: theme park computer graphics.
There was a lot of hope for a breakout from arcade games into full-scale
Virtual Reality rides, and special demos and literature were prepared.
I also was preparing for the conference, in a number of ways.
- prepping for my job
I had learned a lesson from the previous year's AVS User Group Conference
in Orlando: if you want to avoid having your travel cut from a conference
budget at the last minute, arrange to be delivering a talk at the conference.
I knew that SIGGRAPH had a new venue called "technical sketches" with
a late deadline (mid-spring) and I knew that AVS's new product, AVS Express,
was due to be announced in that time frame, so I convinced the folks in
marketing to let me collaborate with Jeff Vroom, the main developer, on
a talk for the July SIGGRAPH conference. I wrote the first draft and then
emailed it to Jeff, who gutted it and wrote a great short paper. I do
take full credit for getting the ball rolling; if not for my efforts it
wouldn't have happened.
- prepping for my family
We decided my wife and infant daughter would come with me to the
conference, at our expense of course, but their motel costs would
be zero. We managed to borrow a folding stroller which was a lifesaver.
We could take it on buses, and our daughter could sleep in it.
Remembering earlier epiphanies about keeping in touch with real
family while visiting a fantasy land, I contacted my Florida cousins
and arranged side trips to visit them on the Space Coast.
prepping for the panel
- planning
As chronicled previously, I did some advance planning while observing
low-tech interactive entertainment at Universal Hollywood and Knott's Berry
Farm. I decided to schedule a birds-of-a-feather, which anyone could attend
without a conference badge, and run it like a panel. The title would be
"The VActor and the Human Factor" and I would endeavor to unite engineers
desinging the technology with actors who operated it to explore early lessons
learned. I also wanted to include actors from the Adventurer's Club.
- paperwork
I got the birds-of-a-feather paperwork into SIGGRAPH by FAX, and they
approved it in time for it to be in the main program. I began working
on the list of participants, guided by some astute friends, including
Richard Cray, Greg Panos and Steve Tice.
- dialing for panelists
Almost on a lark I called Disney Imagineering n Glendale, California and
asked for Joe Rohde, the mad genius behind the Adventurer's Club. He is
rumored to have been in both group portraits in the library there.
( en.wikipedia.org/wiki/Joe_Rohde )
I never spoke with him but I conveyed messages back and forth through his
assistant, who was very helpful. I asked if Joe was going to SIGGRAPH in
Orlando, and she said Joe wanted to know, "What's a SIGGRAPH?"
(Twelve years later Joe gave the keynote speech at SIGGRAPH 2006 in Boston,
_www.siggraph.org/s2006/main.php?f=conference&p=keynote
entitled "From Myth to Mountain: Insights Into Virtual Placemaking," about
his new Expedition Everest project at Disney's Animal Kingdom in Orlando.)
I eventually determined Joe wouldn't be able to participate in my panel,
but he did give his approval for the Adventurer's Club actors to take
part.
I had wanted to get Steve Tice to participate, since he'd founded
Simgraphics and they'd demonstrated the Performance Cartoon of Suzy
Surfer a.k.a. Silver Suzy Machinima at SIGGRAPH '91 in Las Vegas.
But Steve said he'd probably be too busy at SIGGRAPH (he always booked
as many meetings as possible with potential clients) and he recommended
I get Brad deGraf, who said really invented the Performance Cartoon,
in a prototype test of an "electronic puppet" in real time of Kermit the
Frog with Jim Henson and a vector display from Evans and Sutherland.
( http://www.mediaventure.org/docs/degraf-cv.html )
Steve knew Brad and provided an introduction that "greased the skids"
in getting him to agree to participate.
From the Adventurer's Club I confirmed Ann Hering (my contact) who
played the Maid as well as Samantha Sterling and Pamelia Perkins, and
through her Kristian Truelsen who played Hathaway Brown and Graves the
Butler, among others, and Art Doheny, who played the Adventurer from
Sandusky, Ohio, Emil Bleehall.
I rounded out the panel with myself (representing the aerospace/human
factors field) and Richard Cray, who'd operated VActor technology for
Simpgraphics at trade shows.
- a poster for the panel

 the VActor panel poster
As the conference approached I got to work on a promotional poster for the
panel. I wanted to use an image of Pinnochio, but I knew better than to rip
off Disney's intellectual property at a conference they would most certainly
hear about. I went back to their source material and used an image from the
original children's book, thinking that publisher might be a little less
vigilant than Disney.
Luckily I showed my artwork to Greg Panos before I left town. "Did
you know VActor is a trademark of Simgraphics?" he asked me. I had not.
Luckily there was time to add a TM and a footnote.
the VActor panel poster
As the conference approached I got to work on a promotional poster for the
panel. I wanted to use an image of Pinnochio, but I knew better than to rip
off Disney's intellectual property at a conference they would most certainly
hear about. I went back to their source material and used an image from the
original children's book, thinking that publisher might be a little less
vigilant than Disney.
Luckily I showed my artwork to Greg Panos before I left town. "Did
you know VActor is a trademark of Simgraphics?" he asked me. I had not.
Luckily there was time to add a TM and a footnote.
a last-minute connection
I've related how I once went to a party at Maxine Brown's in L.A., dragged
there by Greg Panos, and I didn't know yet who she was. Well, she moved
back to Illinois and joined the Electronic Visualization Laboratory at the
University of Illinois at Chicago with Tom deFanti.
( en.wikipedia.org/wiki/Electronic_Visualization_Laboratory )
Well, they were working on this Virtual Reality demonstration called the
VROOM (Virtual ROOM) and they wanted to integrate it with AVS software, but
they'd hit a technical snag. Maxine remembered she was two degrees of
separation from me, apparently, and called me up. I put her in touch with
AVS software engineer Jeff Vroom because it seemed to make karmic sense.
prepping for me
I used to approach near-hysteria as a SIGGRAPH conference grew near.
(Nowadays I've calmed right down.) One way I burned off excess energy
was by making mix tapes on cassette for the trip. In addition to the
above CDs I'd also bought the brand-new "Fruitcakes" (May 1994) by Jimmy
Buffett.
( www.amazon.com/exec/obidos/ASIN/B000002OS8/hip-20 )
With these and other sources I began making a 90-minute tape, which grew
into a set of tapes, ultimately four 90-minute cassettes long, or six
hours for Pete's sake. I called the set "Serious Fun," a slogan for
Silicon Graphics Inc. (SGI), and each tape had a subtitle:
- Destination Resort
- Location-Based Entertainment
- Sponge-O-Rama
- I'm Just Drawn That Way
(And as if that wasn't enough, I made a fifth and sixth tape, "Grand
Floridian" and ""Remembering the Future" upon returning home.)
SIGGRAPH 1994
 Orange County Convention Center map
Orange County Convention Center map
"Afterwards I saw two teenagers at the trolley stop; one was holding a
cigarette. The other asked, 'You need a light?' His friend answered,
'No, I've got a lighter. I'm just too tired to smoke.' Even though I
don't smoke myself, I knew what he meant."
— Alan Scrivener "They're Cutting Corners in 2003 ~or~ A Long,
Hard Look At the Future of the SIGGRAPH Conference"
( san-diego.siggraph.org/articles/SG2003/sg2003.html )
The actual week of SIGGRAPH, July 24-29, 1994, was one of the most enjoyable
and intense weeks of my life. Words cannot describe, but I'll try.
- booth duty
AVS Inc. flew me there, and AVS put me to work. I help set up hardware,
install demos, verify demos, and work in the trade show booth meeting
prospects and talking to them about their needs and our offerings, and
giving demos.
- AVS Exress "technical sketch"
I showed up for the tech talk that I was listed as co-author on. Jeff
delivered it to a packed house. I was glad there was such interest in
the community in our new product. I was also proud that I'd catalyzed the
event. And I was glad the bean counters hadn't figured out they didn't
really have to fly me to Orlando unless Jeff couldn't make it.
- the $1.8 million deal
Even while the conference proceeded I also had work to do for the
southern California sales office of AVS (near John Wayne Airport in
Irvine, California). We were working on closing a deal for $1.8 million
worth of software for Adac Laboratories, a company that makes Gamma Cameras
for medical imaging, recording gamma rays after a patient swallows a
"nuclear cocktail."
( en.wikipedia.org/wiki/ADAC_Laboratories )
Without a cell phone I had to wait in line for phone booths, communicating
with the Adac folks several times a day, relaying questions to the
engineers (some at HQ in Waltham, Massachusetts, and some at the conference
with me in Orlando) and relay answers back. I didn't drop anything out.
Later, when the order was completed, the Vice President of Engineering
aknowledged in front of the assembled sales department that I had been the
sole technical contact with Adac for the entire sale, which was a record for
the company.
- hangin' with Phil C.
My good friend Phil C. (who passed away at the beginning of this year, alas)
was attending the conference for the Scripps Research Institute, where he was
head of IT, and they got him a very nice suite at the Gaylord. He invited me
and some other friends to hang out on the first night (Sunday), and I brought
my boom box and my mix tapes. Of course we didn't have time for all six
hours. But one song was a huge hit, given our companions and our locale: a
cover of the Grateful Dead's "Uncle John's Band" by Mr. Margaritaville,
Jimmy Buffet.
Later in the week Phil joined my wife, daughter and me for an afternoon
at what was then called Disney-MGM Studios theme park, where we rode
the Twilight Zone Tower of Terror for the first and second time.
Phil said the park's architecture based on L.A. and Hollwood in the '20s and
'30s reminded him of his youth, growing up near downtown L.A. in the '50s.
After that we soaked in the pool at our hotel in the warm evening, and
he told us about a talk at the conference by Terrence McKenna, in which
he talked about "remembering the future."
- the Mindtel van
My friend and colleague Dave Warner arrived with a van full of people and
equipment after a cross-country trip from San Diego to Orlando, and approached
the organizers of "the Edge" emerging technology demo area for some space.
They explained it was a juried exhibition, with the selections announced
months ago, and there was no way. Then they let him in anyway.
- Tanged demo loop
I turned out there were folks at Disney that knew about SIGGRAPH; they had
a booth, and they were recruiting for Animation and Imagineering. They also
had an impressive computer-generated loop playing of Rapunzel's hair from
"Tangled" flying in a breeze — sixteen years before the movie was
released!
- VROOM
 the CAVE, a sort of VROOM
( en.wikipedia.org/wiki/Electronic_Visualization_Laboratory )
I got to experience the VROOM (Virtual ROOM) from the Electronic
Visualization Laboratory, running the AVS software, and flying over
Chicago and through molecules with three screens wrapping around and
one above, plus 3D glasses. Jeff Vroom did help them get it working,
and he got to experience it too.
the CAVE, a sort of VROOM
( en.wikipedia.org/wiki/Electronic_Visualization_Laboratory )
I got to experience the VROOM (Virtual ROOM) from the Electronic
Visualization Laboratory, running the AVS software, and flying over
Chicago and through molecules with three screens wrapping around and
one above, plus 3D glasses. Jeff Vroom did help them get it working,
and he got to experience it too.
- the Kubota Pacific implosion
Kubota Pacific Computing, a company I'd left to join AVS in 1992, had
a big booth at SIGGRAPH '94, showing a kick-a** racecar simulation
with a real racecar cockpit. They collected a lot of leads on sheets
of NCR paper (like carbon paper but inkless) over the week. On the last
day they found out that the Japanese parent company was shutting them down,
and they were all being laid off. The tore their lead sheets into confetti
and threw it into the air.
- time delay in VActor(TM) technology
It wasn't until I was showing Adventurer's Club actor Kris Truelsen
the VActor display in the "the Edge" (new technology demos) at SIGGRAPH
that I noticed there was a time delay in the audio, so it stayed synced
with the video which had some latency due the rendering speed. Hmmm.
- SIGKids
I noticed that the '94 conference had a SIGKids venue set up right at the
front of the convention center, outside of the exhibit hall, but I never
got a chance to go in and check it out. I saw kids soldering. (It was
chaired by Nancy Ingle of the Orange County Public Schools.)
- daughter's first word
Our daughter C., at the age of 11 months, heard me say "duck" while
pointing at a duck, and repeated it. We were strolling around the
grounds and waters of the Disney Caribbean Beach Resort, and my wife had
just wandered off. "I hope she does it again when mom comes back," I
thought. And she did, very clearly!
- visiting cousins
I got to see my first cousins (dad's brother's kids) Beth and Charles
who I've known all their lives, plus their kids, and they got to see
our new daughter.
- showing up for the panel
I was glad the VActor panel was on Monday, so I wouldn't have to be nervous
all week. We showed up early to the Peabody Hotel, both to double-check the
venue, and because I hadn't written my introductory remarks. On the way in
we crossed duckprints painted on the sidewalk at a Duck Crossing. In the
lobby ducks were in the fountain. It turns out this was a big deal to the
Peabody Hotel, a copy of the original in Memphis, Tennessee.
( en.wikipedia.org/wiki/Peabody_Hotel )
We found a sort-of malt shop and took a seat and had a snack while I took
notes on a place mat. The menu said the ducks were "live decoys," and I had
a hunch there was a a way to work this into my talk, but I couldn't see the
connection.
It was time. We went to the location, and saw that a good-sized crowd for the
room size was assembling. All of our panelists were prompt. "I'll speak
first and then give you each ten minutes," I said. Brad and Richard,
veterans of many conferences, nodded. The three actors looked like deer in
the headlights. "We have to speak?" Ann asked. I told them they were
masters of improvisation, and I would call on them last to give them time.
I took the podium.
TO BE CONTINUED...
========================================================================
newsletter archives:
www.well.com/user/abs/Cyb/archive
========================================================================
Privacy Promise: Your email address will never be sold or given to
others. You will receive only the e-Zine C3M from me, Alan Scrivener,
at most once per month. It may contain commercial offers from me.
To cancel the e-Zine send the subject line "unsubscribe" to me.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I receive a commission on everything you purchase from Amazon.com after
following one of my links, which helps to support my research.
========================================================================
Copyright 2016 by Alan B. Scrivener
Last update:
Thu Dec 1 19:44:17 PST 2016
illustration from Unspy blog (unspy.wordpress.com/tag/fourth-amendment/)
"Fractured Flickers" letterhead with Theda Bara (artofjayward.blogspot.com/2015/06/fractured-flickers.html)
 On October 23, 2016 a new book by Nora Bateson, daughter of Gregory Bateson,
became available on Amazon: "Small Arcs of Larger Circles: Framing Through
Other Patterns."
( www.amazon.com/exec/obidos/ASIN/1909470961/hip-20 )
She also has a blog at:
norabateson.wordpress.com/
and is on Facebook.
On October 23, 2016 a new book by Nora Bateson, daughter of Gregory Bateson,
became available on Amazon: "Small Arcs of Larger Circles: Framing Through
Other Patterns."
( www.amazon.com/exec/obidos/ASIN/1909470961/hip-20 )
She also has a blog at:
norabateson.wordpress.com/
and is on Facebook.
 NY Times photo
(Note: in the few weeks since I typed the above, Dr. Forrester passed away.
www.nytimes.com/2016/11/18/technology/jay-forrester-dead.html?_r=0
I will have more to say about this remarkable man in an upcoming 'zine.)
NY Times photo
(Note: in the few weeks since I typed the above, Dr. Forrester passed away.
www.nytimes.com/2016/11/18/technology/jay-forrester-dead.html?_r=0
I will have more to say about this remarkable man in an upcoming 'zine.)
 illustration for "What Is Encryption?" from wiseGEEK
( www.wisegeek.com/what-is-encryption.htm )
illustration for "What Is Encryption?" from wiseGEEK
( www.wisegeek.com/what-is-encryption.htm )
 Dilbert cartoon
( https://www.random.org/analysis/ )
Dilbert cartoon
( https://www.random.org/analysis/ )
 4096 frequencies as brightness values
4096 frequencies as brightness values
 money growing on trees?
( www.digitaltrends.com/cool-tech/amazon-kickstarter-site/ )
money growing on trees?
( www.digitaltrends.com/cool-tech/amazon-kickstarter-site/ )
 cyberthief
( www.hackguide4u.com/2010/09/huge-collection-of-hacking-ebooks.html )
cyberthief
( www.hackguide4u.com/2010/09/huge-collection-of-hacking-ebooks.html )
 the eye in the triangle
( www.pinterest.com/magda1316/illuminati/ )
the eye in the triangle
( www.pinterest.com/magda1316/illuminati/ )

 got the tee shirt
got the tee shirt
 SIGGRAPH '94 logo
SIGGRAPH '94 logo

 the VActor panel poster
As the conference approached I got to work on a promotional poster for the
panel. I wanted to use an image of Pinnochio, but I knew better than to rip
off Disney's intellectual property at a conference they would most certainly
hear about. I went back to their source material and used an image from the
original children's book, thinking that publisher might be a little less
vigilant than Disney.
Luckily I showed my artwork to Greg Panos before I left town. "Did
you know VActor is a trademark of Simgraphics?" he asked me. I had not.
Luckily there was time to add a TM and a footnote.
the VActor panel poster
As the conference approached I got to work on a promotional poster for the
panel. I wanted to use an image of Pinnochio, but I knew better than to rip
off Disney's intellectual property at a conference they would most certainly
hear about. I went back to their source material and used an image from the
original children's book, thinking that publisher might be a little less
vigilant than Disney.
Luckily I showed my artwork to Greg Panos before I left town. "Did
you know VActor is a trademark of Simgraphics?" he asked me. I had not.
Luckily there was time to add a TM and a footnote.
 Orange County Convention Center map
Orange County Convention Center map
 the CAVE, a sort of VROOM
( en.wikipedia.org/wiki/Electronic_Visualization_Laboratory )
I got to experience the VROOM (Virtual ROOM) from the Electronic
Visualization Laboratory, running the AVS software, and flying over
Chicago and through molecules with three screens wrapping around and
one above, plus 3D glasses. Jeff Vroom did help them get it working,
and he got to experience it too.
the CAVE, a sort of VROOM
( en.wikipedia.org/wiki/Electronic_Visualization_Laboratory )
I got to experience the VROOM (Virtual ROOM) from the Electronic
Visualization Laboratory, running the AVS software, and flying over
Chicago and through molecules with three screens wrapping around and
one above, plus 3D glasses. Jeff Vroom did help them get it working,
and he got to experience it too.